HTTPS ciphers suite 的选择要奉行一个原则: 安全 兼容 性能
可以参考https://wiki.mozilla.org/Security/Server_Side_TLS#Recommended_configurations 这个链接
| Configuration | Oldest compatible client |
|---|---|
| Modern | Firefox 27, Chrome 30, IE 11 on Windows 7, Edge, Opera 17, Safari 9, Android 5.0, Java 8 |
| Intermediate | Firefox 1, Chrome 1, IE 7, Opera 5, Safari 1, Windows XP IE8, Android 2.3, Java 7 |
| Old | Windows XP IE6, Java 6 |
如果是个人网站,不需要考虑支持较老和古老的浏览器,直接选择Modern支持即可
对于大多数的网站来说,还是需要综合考量的,先假设只需要支持modern和Intermediate
Intermediate compatibility (default)
For services that don’t need compatibility with legacy clients (mostly WinXP), but still need to support a wide range of clients, this configuration is recommended. It is is compatible with Firefox 1, Chrome 1, IE 7, Opera 5 and Safari 1.
- Ciphersuites: ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:ECDHE-ECDSA-DES-CBC3-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:DES-CBC3-SHA:!DSS
- Versions: TLSv1.2, TLSv1.1, TLSv1
- TLS curves: prime256v1, secp384r1, secp521r1
- Certificate type: RSA
- Certificate curve: ‘None
- Certificate signature: sha256WithRSAEncryption
- RSA key size: 2048
- DH Parameter size: 2048
- ECDH Parameter size: 256
- HSTS: max-age=15768000
- Certificate switching: None
几个关键点:
- RSA key 用2048的签名就可以了
- DH 用2048
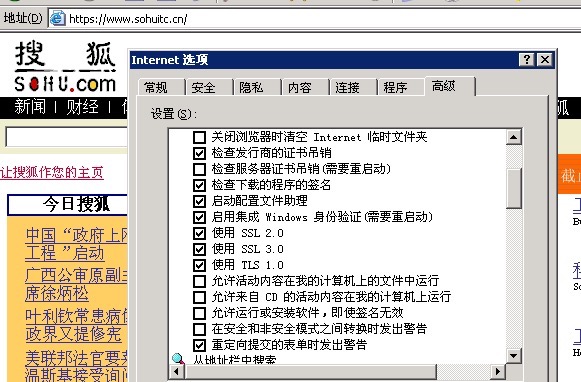
- 使用TLS1.0-1.2, 不要使用不安全的SSLv2-3
- 加密的cipher-suite 可以参考以上,也可以自己调整顺序,比如可以根据自己客户端是PC浏览器多还是移动端多,把CHACHA挪后…
参考资料:
https://wiki.mozilla.org/Security/Server_Side_TLS#Recommended_configurations